PuTTY SSH ProxyCommand
May 20, 2020 – 11:07I’ve had problems in the past, where I’ve had so many NAT configurations to get into various machines in my small, home network. Using the ssh ProxyCommand, you can use a single exposed machine to forward your...
PuTTY Advanced download
May 20, 2020 – 11:06PuTTY is the most popular SSH client for Windows. One, and probably the only one, of PuTTY drawbacks is that you need to start a new copy of PuTTY every time you open a new connection. So if you need e.g. 5 active...
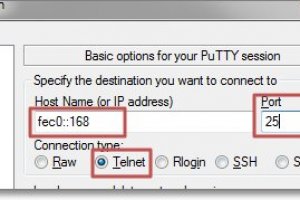
PuTTY IPv6
May 20, 2020 – 11:07Summary: Reported X forwarding breakage due to IPv6 class : bug: This is clearly an actual problem we want fixed. difficulty : taxing: Needs external things we dont have (standards, users etc) priority : medium:...
PuTTY Download chip
May 20, 2020 – 11:07SuperPuTTY Aims to enhance the capabilities of the PuTTY SSH and Telnet client by allowing you to launch it in multiple tabs. It offers you the possibility to easily manage multiple sessions of PuTTY using a single,...
PuTTY agent download
May 20, 2020 – 11:07Pageant is designed to ease the use of PuTTY, PSCP, Plink and PSFTP, providing a SSH authorization agent ready to store all your private keys within a secure place. The main advantage to this is that you dont have...
Download PuTTY HP
May 20, 2020 – 11:07HPE Network Automation software automates the complete operational lifecycle of network devices from provisioning to policy-based change management, compliance, and security administration. When combined with HPE...
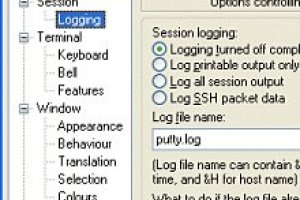
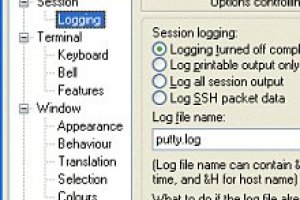
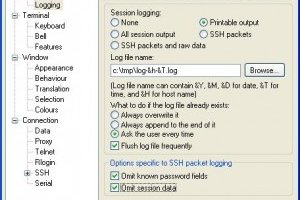
PuTTY log
May 20, 2020 – 11:07Putty has the option to log telnet and SSH traffic session output to disk. I think it’s a good idea to always log the telnet and SSH session output of every session to a file. In this way you always have a great...
PuTTY SSH manual
May 20, 2020 – 11:06PuTTY is a free (MIT-licensed) Win32 Telnet and SSH client. This manual documents PuTTY, and its companion utilities PSCP, PSFTP, Plink, Pageant and PuTTYgen. Note to Unix users: this manual currently primarily...
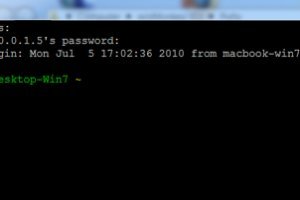
PuTTY SSH tunnel RDP
May 20, 2020 – 11:06Lets assume the following:Linux Server - gate.college-server.com:22 (SSH listens on port 22)Internal Server - internal.college-server.com:3389 (RDP listens on port 3389)RDP connection will be on localhost:3399 (should...
PuTTY download connection Manager
May 20, 2020 – 11:07This article is part of the on-going Software For Geeks series. PuTTY Connection Manager was mentioned in the 12 PuTTY add-ons that we discussed a while back. One of the major missing features in PuTTY is the ability...
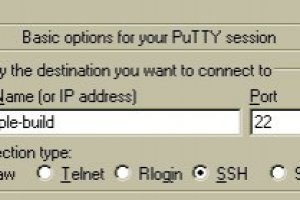
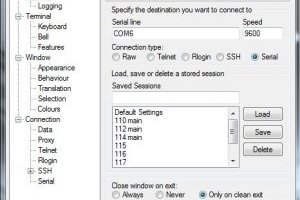
Putty SSH connection
May 20, 2020 – 11:07After this start puttygen.exe and click on the Load button. Select the private_key.ppk file that you have previously created with your private key and click on the Open button. You will be prompted for the passphrase...
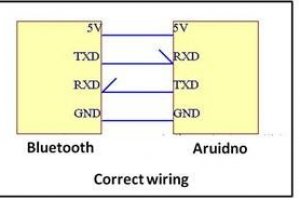
PuTTY Bluetooth download
May 20, 2020 – 11:06Notre rseau a dtect que vous tes localis en France. SlashdotMedia accorde de l’importance la vie prive de nos utilisateurs. Les lois franaises exigent que nous obtenions votre permission avant denvoyer des cookies...
Download PuTTY version 0.63
May 20, 2020 – 11:07USER REVIEWS No user reviews were found. This free software does not only give you the option of connecting to different systems, but PuTTY Portable also allows you to execute different programs from a distance....